Run DLL error message/background container.dll
There was a problem starting
c:\users\ed\appData\local\conduit\backgroundcontainer\background container.dll
WHY
The error message is triggered by a scheduled task that is left behind after removing the Conduit Malware. Because it is a scheduled task at Startup that autorun and looks for the missing BackgroundContainer.dll, the system brings up the error message. And because it is a routine task scheduled in your system's Task Library, malware removal software will not flag it as malware. Therefore, running malware software will not fix it, but can create the issue by removing the file What you need to do is simply delete the task so it won't be executed at startup.
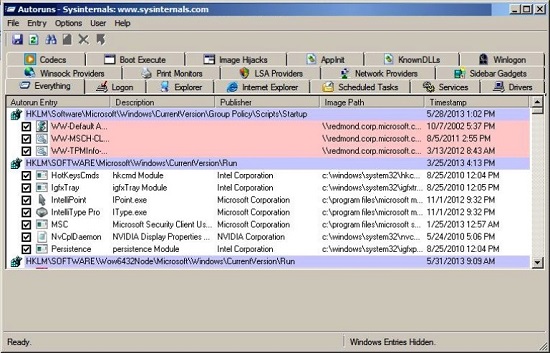
Once you install it and launch the application, you can see a complete list of
all autorun items (the default is the Everything tab). Note: it may take a few
seconds for it to display the results.
The Autoruns application will show multiple tabs, each representing a specific
group of items. Click on the Scheduled Tasks tab to see only the scheduled
autorun tasks. One of the entries is the above mentioned DLL reference
(BackgroundContainer.dll). Uncheck the checkbox to the left of the entry and
then delete the entry/task. Restart your system and it should be gone.
Autoruns for Windows v11.70
|
DOWNLOAD IT
OTHER INFORMAITON
Introduction
This utility, which has the most comprehensive knowledge of
auto-starting locations of any startup monitor, shows you what programs
are configured to run during system bootup or login, and shows you the
entries in the order Windows processes them. These programs include ones
in your startup folder, Run, RunOnce, and other Registry keys. You can
configure Autoruns to show other locations, including Explorer shell
extensions, toolbars, browser helper objects, Winlogon notifications,
auto-start services, and much more. Autoruns goes way beyond the
MSConfig utility bundled with Windows Me and XP.
Autoruns' Hide Signed Microsoft Entries option helps you to zoom in on
third-party auto-starting images that have been added to your system and
it has support for looking at the auto-starting images configured for
other accounts configured on a system. Also included in the download
package is a command-line equivalent that can output in CSV format,
Autorunsc.
You'll probably be surprised at how many executables are launched
automatically!
Usage
See the November 2004 issue of Windows IT Pro Magazine for Mark's
article that covers advanced usage of Autoruns. If you have questions or
problems, visit the Sysinternals Autoruns Forum.
Simply run Autoruns and it shows you the currently configured auto-start
applications as well as the full list of Registry and file system
locations available for auto-start configuration. Autostart locations
displayed by Autoruns include logon entries, Explorer add-ons, Internet
Explorer add-ons including Browser Helper Objects (BHOs), Appinit DLLs,
image hijacks, boot execute images, Winlogon notification DLLs, Windows
Services and Winsock Layered Service Providers. Switch tabs to view
autostarts from different categories.
To view the properties of an executable configured to run automatically,
select it and use the Properties menu item or toolbar button. If Process
Explorer is running and there is an active process executing the
selected executable then the Process Explorer menu item in the Entry
menu will open the process properties dialog box for the process
executing the selected image.
Navigate to the Registry or file system location displayed or the
configuration of an auto-start item by selecting the item and using the
Jump menu item or toolbar button.
To disable an auto-start entry uncheck its check box. To delete an
auto-start configuration entry use the Delete menu item or toolbar
button.
Select entries in the User menu to view auto-starting images for
different user accounts.
More information on display options and additional information is
available in the on-line help.
Autorunsc Usage
Autorunsc is the command-line version of Autoruns. Its usage syntax is:
Usage: autorunsc [-x] [[-a] | [-b] [-c] [-d] [-e] [-g] [-h] [-i] [-k]
[-l] [-m] [-o] [-p] [-r] [-s] [-v] [-w] [[-z <systemroot> <userprofile>]
| [user]]]
-a Show all entries.
-b Boot execute.
-c Print output as CSV.
-d Appinit DLLs.
-e Explorer addons.
-g Sidebar gadgets (Vista and higher).
-h Image hijacks.
-i Internet Explorer addons.
-l Logon startups (this is the default).
-m Hide signed Microsoft entries.
-n Winsock protocol and network providers.
-p Printer monitor drivers.
-r LSA providers.
-s Autostart services and non-disabled drivers.
-t Scheduled tasks.
-v Verify digital signatures.
-w Winlogon entries.
-x Print output as XML.
-z Specifies the offline Windows system to scan.
user Specifies the name of the user account for which autorun items will
be shown.